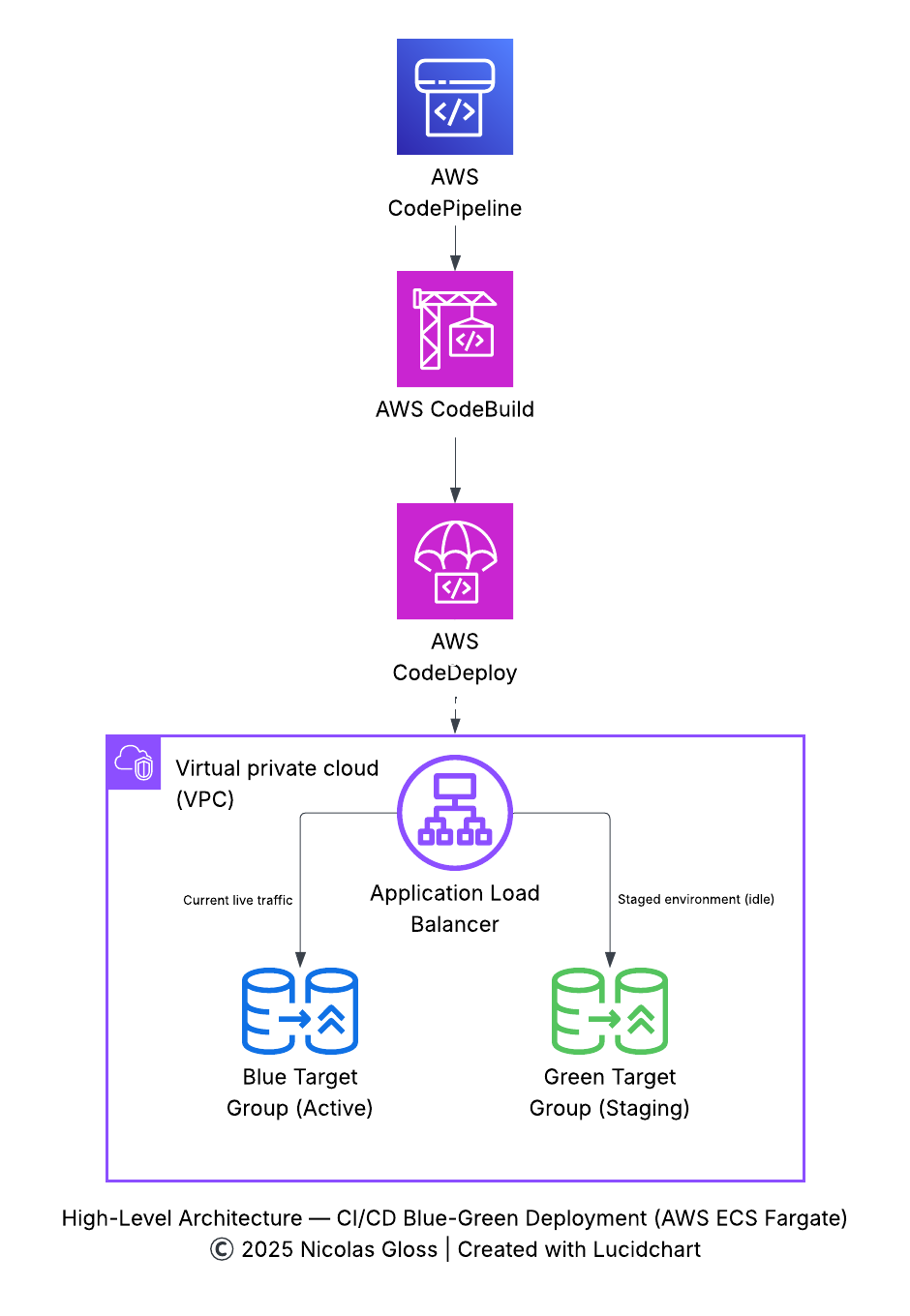
 High-level architecture of the CI/CD Blue-Green deployment (exported from Lucidchart).
High-level architecture of the CI/CD Blue-Green deployment (exported from Lucidchart).
🚀 Overview
This project delivers a complete CI/CD Blue-Green deployment pipeline for containerised workloads running on AWS ECS Fargate, with the entire infrastructure defined using AWS CDK (TypeScript).
It demonstrates:
- Zero-downtime deployments using CodeDeploy traffic shifting
- Infrastructure as Code with modular, testable CDK stacks
- Automated CI with GitHub Actions + CodePipeline
- End-to-end validation through Jest tests and AWS Console checks
This mirrors real-world cloud engineering and DevOps practices used in production environments.
🧱 AWS Services Used
| Service | Purpose |
|---|---|
| AWS CDK (TypeScript) | Defines the entire pipeline and ECS infrastructure as code. |
| Amazon ECS Fargate | Serverless compute platform for running containers. |
| AWS CodePipeline + CodeBuild | Builds, synthesises, and deploys application updates from GitHub. |
| AWS CodeDeploy | Orchestrates Blue/Green traffic shifting between target groups. |
| Application Load Balancer (ALB) | Routes traffic to the active environment (Blue or Green). |
| AWS Secrets Manager | Stores the GitHub access token securely. |
| Amazon VPC | Provides isolated networking for ECS tasks and pipeline components. |
🧩 Key Features
- Fully automated CI/CD pipeline from GitHub commit → build → ECS deployment
- True Blue/Green deployments with CodeDeploy-managed traffic shifting
- 7/7 Jest unit tests verifying stack correctness
- All IaC modularised into VPC, ECS, Service, CodeDeploy, and Pipeline stacks
- Lucidchart architecture diagram included for portfolio clarity
- CDK Synth & Deploy validated across the entire pipeline
🧠 Lessons Learned
- Managing stack dependencies using CDK’s
addDependency() - Coordinating ECS, ALB, and CodeDeploy for seamless Blue/Green releases
- Using target groups and listener rules for zero-downtime switching
- Implementing clean, interview-ready IaC that is easy to iterate on
- Debugging real-world issues with CodeDeploy event logs and ECS health checks
Reflection:
This project strengthened my understanding of end-to-end CI/CD pipelines, advanced ECS deployment strategies, and production-grade IaC structure.
It also deepened my troubleshooting skills across CodePipeline, ALB routing, and ECS task health checks.
🧪 Testing & Validation
- All unit tests run via Jest (
npm run test) - 7/7 unit tests passing, covering VPC, ECS, Service, CodeDeploy, and Pipeline
- CDK Synth confirms clean, error-free infrastructure generation
- Deployed stack verified in AWS Console (CodeDeploy, ECS, ALB)
- Full teardown performed after verification to avoid ongoing charges
🖼️ Screenshots
| Screenshot | Description |
|---|---|
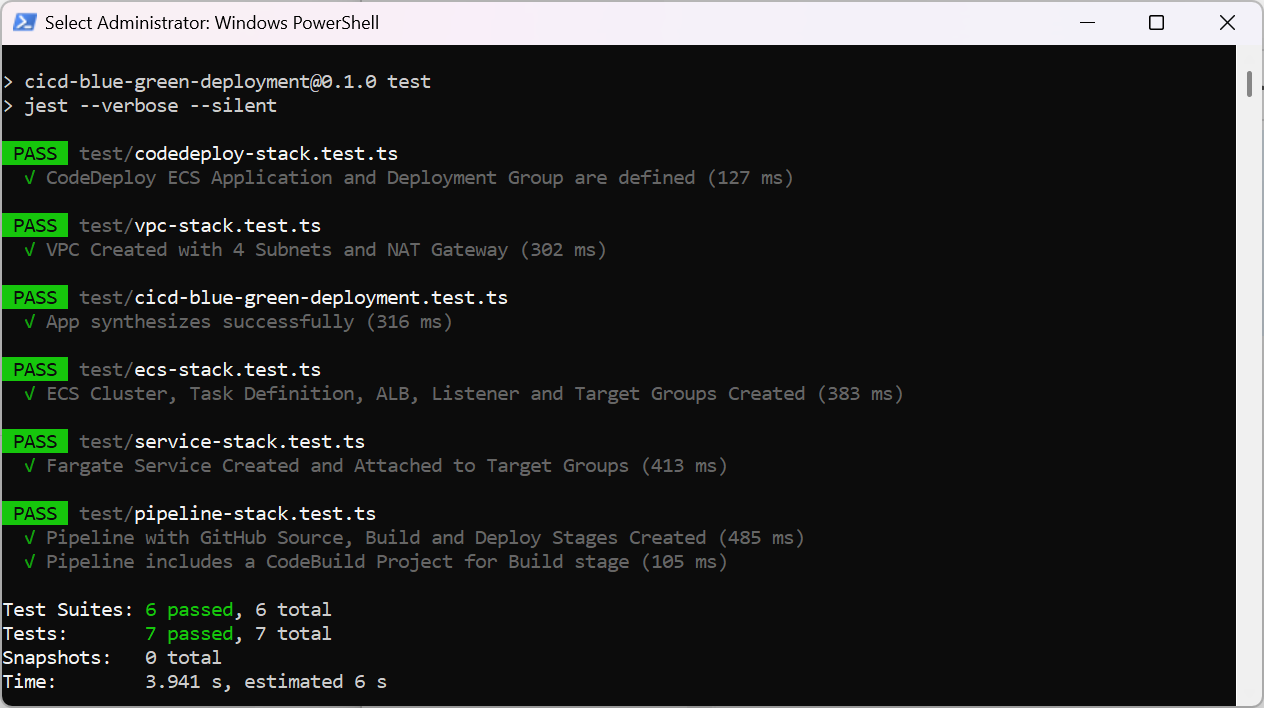 | All Jest tests passed successfully. |
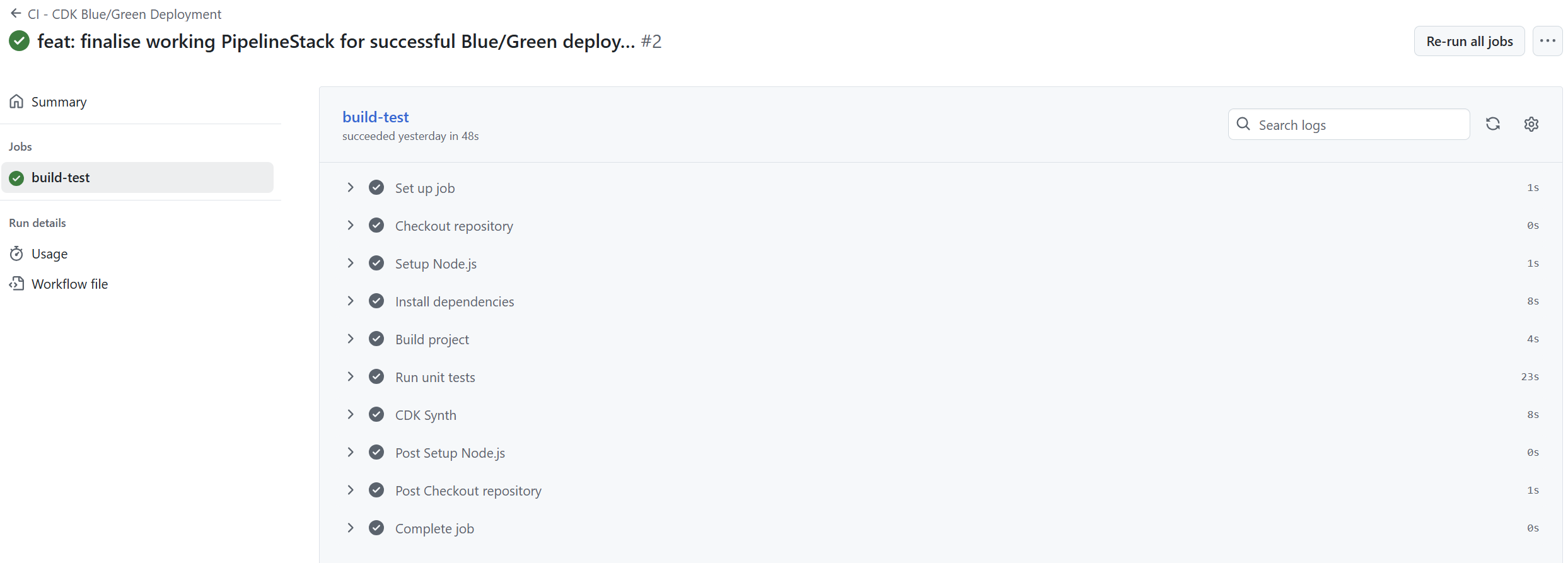 | GitHub Actions CI workflow performing build + tests. |
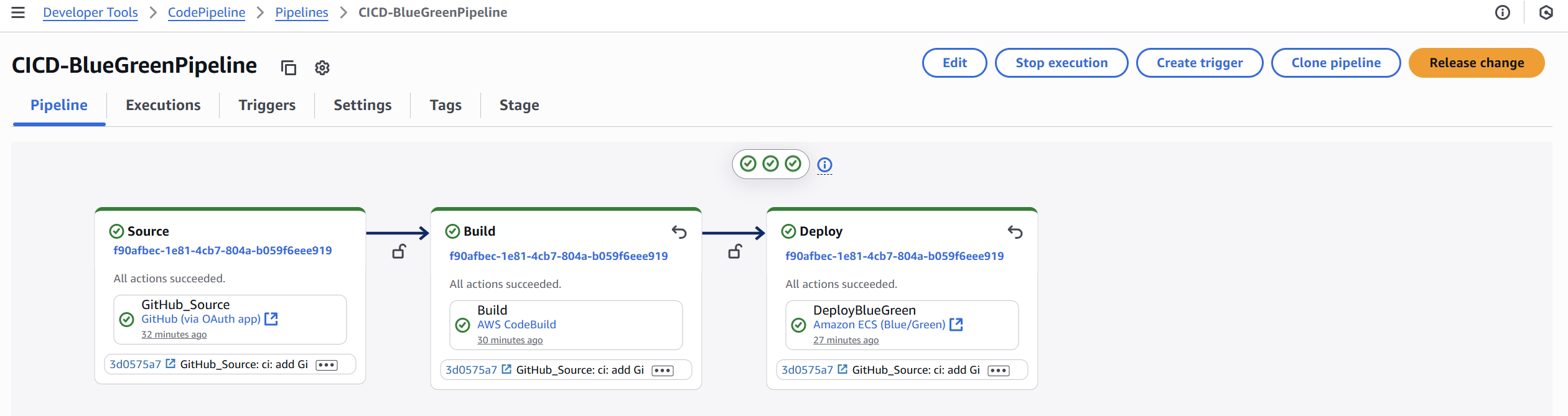 | CodePipeline stages: Source → Build → Deploy. |
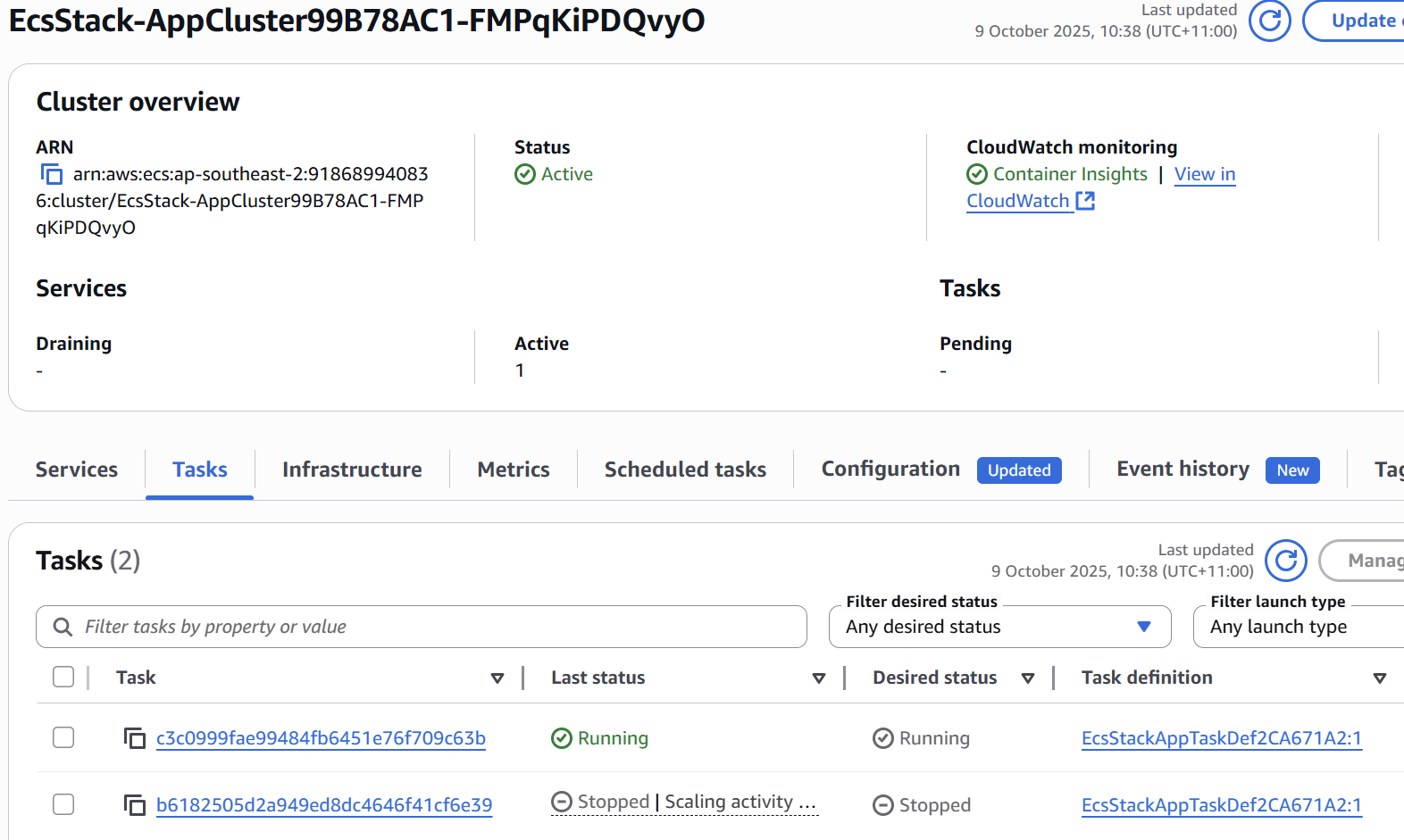 | ECS showing Blue/Green target groups controlled by CodeDeploy. |
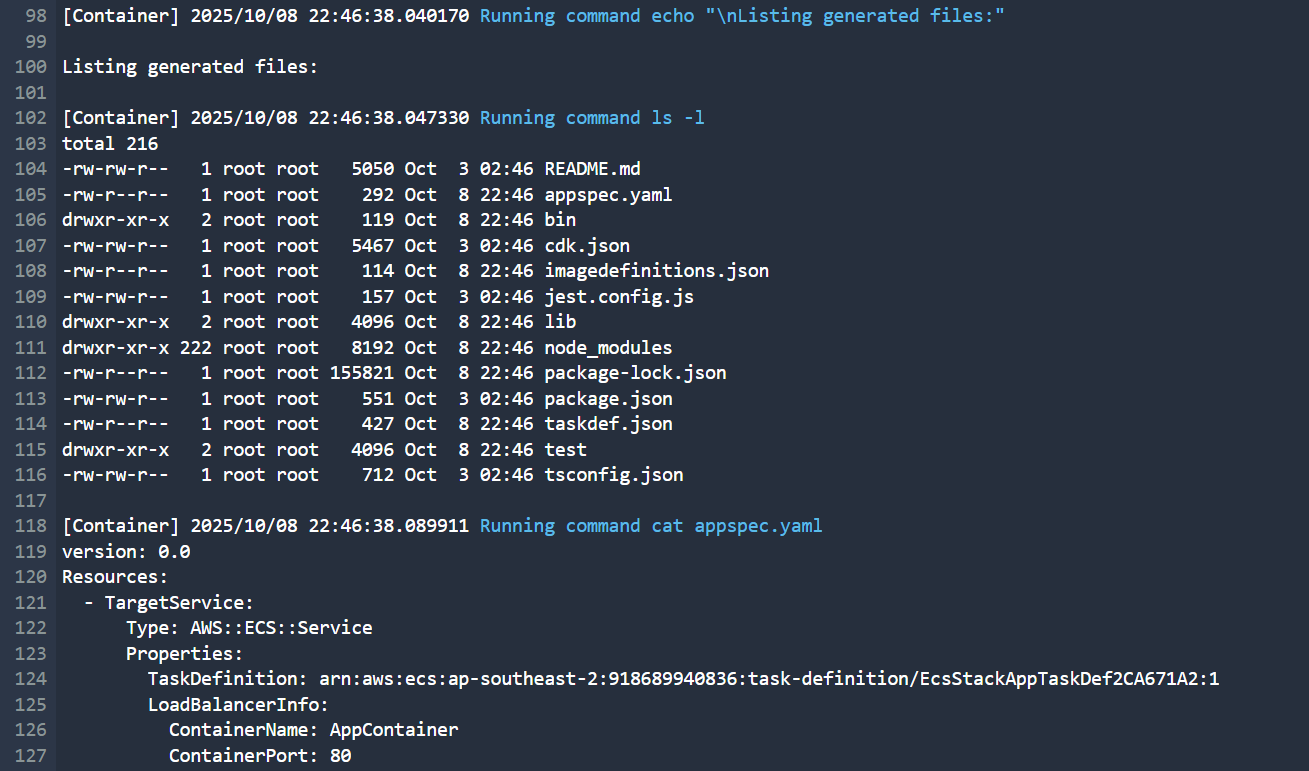 | CodeBuild logs confirming artifact and appspec file generation. |
📘 Documentation
Main README:
https://github.com/nicolasgloss-dev/cicd-blue-green-deployment/blob/main/README.mdDetailed README:
https://github.com/nicolasgloss-dev/cicd-blue-green-deployment/blob/main/docs/README-detailed.mdArchitecture Decision Log (ADR):
https://github.com/nicolasgloss-dev/cicd-blue-green-deployment/blob/main/docs/adr.mdGitHub Release Notes (v1.0.0):
https://github.com/nicolasgloss-dev/cicd-blue-green-deployment/releases/tag/v1.0.0
🏁 Project Status
✅ Stable and Complete (v1.0.0)
All tests passed, architecture validated, and code is fully production-aligned and portfolio-ready.
© 2025 Nicolas Gloss — AWS Cloud Engineer Portfolio
Built and deployed using AWS CDK and Hugo PaperMod.