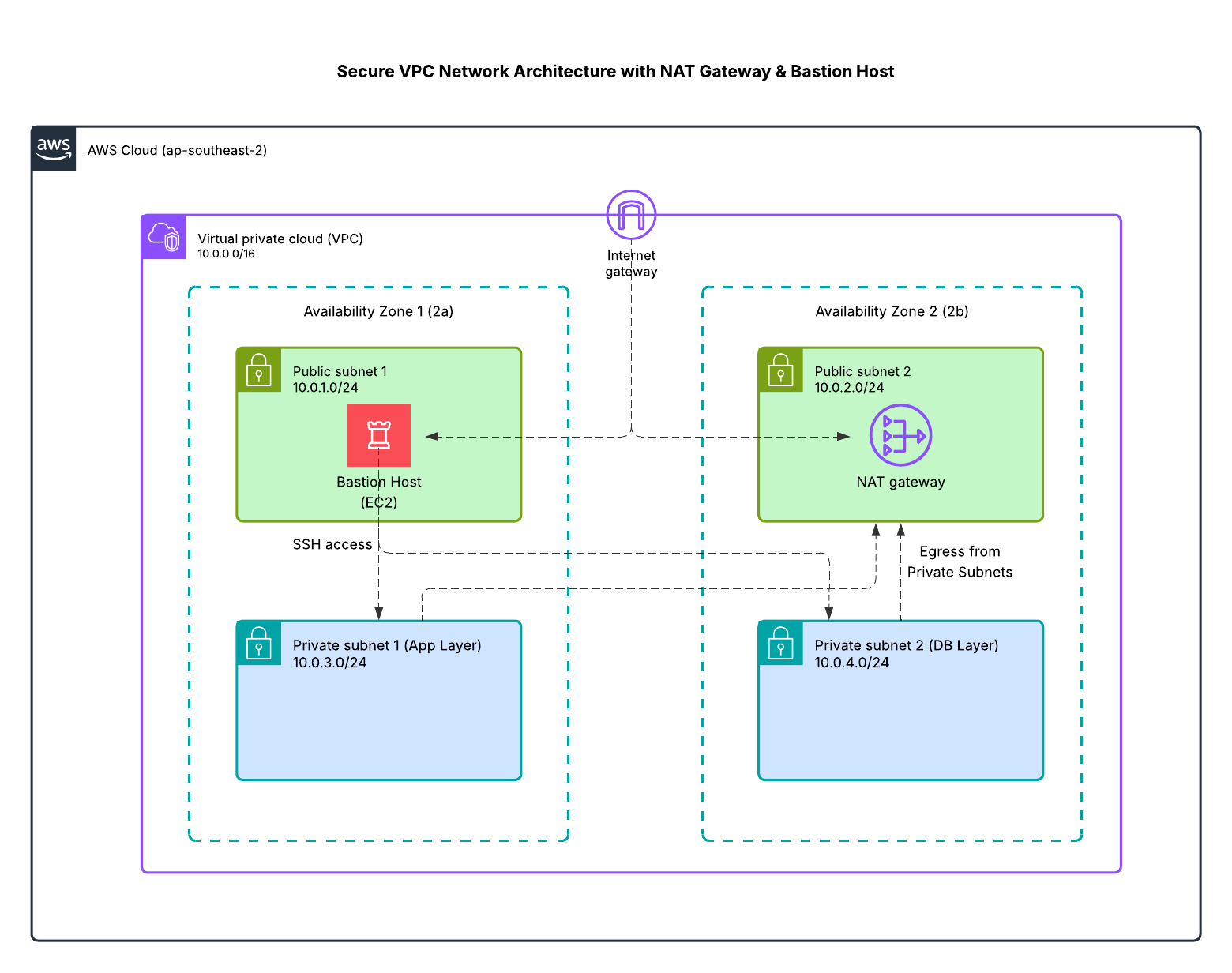
 Architecture diagram showing public/private subnets across two AZs, NAT Gateway, and Bastion Host.
Architecture diagram showing public/private subnets across two AZs, NAT Gateway, and Bastion Host.
🏗️ Overview
This project builds a secure, production-style Virtual Private Cloud (VPC) using AWS CDK (TypeScript).
It implements segmented networking with public and private subnets, secure outbound access via a NAT Gateway, and a Bastion Host for controlled administrative access.
The goal was to create a realistic, foundational cloud network that mirrors what organisations use to host modern workloads.
🧱 AWS Services Used
| Service | Purpose |
|---|---|
| Amazon VPC | Provides an isolated, secure network boundary |
| Public + Private Subnets | Segregate internet-facing and internal workloads |
| Internet Gateway | Enables public subnet internet access |
| NAT Gateway | Allows private subnets outbound internet access |
| EC2 Bastion Host | Controlled SSH administration entry point |
| Security Groups | Enforce least-privilege network rules |
| Route Tables | Manage routing for each subnet |
| AWS CDK (TypeScript) | Infrastructure as Code for repeatable deployments |
🧩 Key Features
✔ Public & Private Subnet Segmentation
Two Availability Zones, each with a public and private subnet, aligned with multi-AZ best practices.
✔ Cost-Aware NAT Gateway
A single NAT Gateway was used to balance cost with functionality — suitable for small projects or proof-of-concept deployments.
✔ Bastion Host for Secure Access
An EC2 instance in the public subnet allows SSH access into private subnets.
Access is restricted by a user-provided CIDR at deploy time.
✔ Clean Infrastructure Outputs
CDK outputs key IDs and a ready-to-use SSH command for convenient testing and validation.
🧠 Business Need
Organisations require secure, isolated network designs to protect internal workloads.
This project addresses real-world needs such as:
- Keeping application servers off the public internet
- Enforcing controlled administrative access
- Providing secure outbound internet for private workloads
- Building a reliable base layer for future cloud deployments
It serves as a foundational network layer for more complex architectures.
🧪 Testing & Validation
- Deployed VPC and Bastion Host via AWS CDK
- Verified:
- Subnet CIDR ranges
- NAT Gateway routing behaviour
- SSH access into private subnets
- Security group ingress/egress rules
- Checked routing tables in AWS Console
- Clean teardown validated using
cdk destroy
🖼️ Screenshots
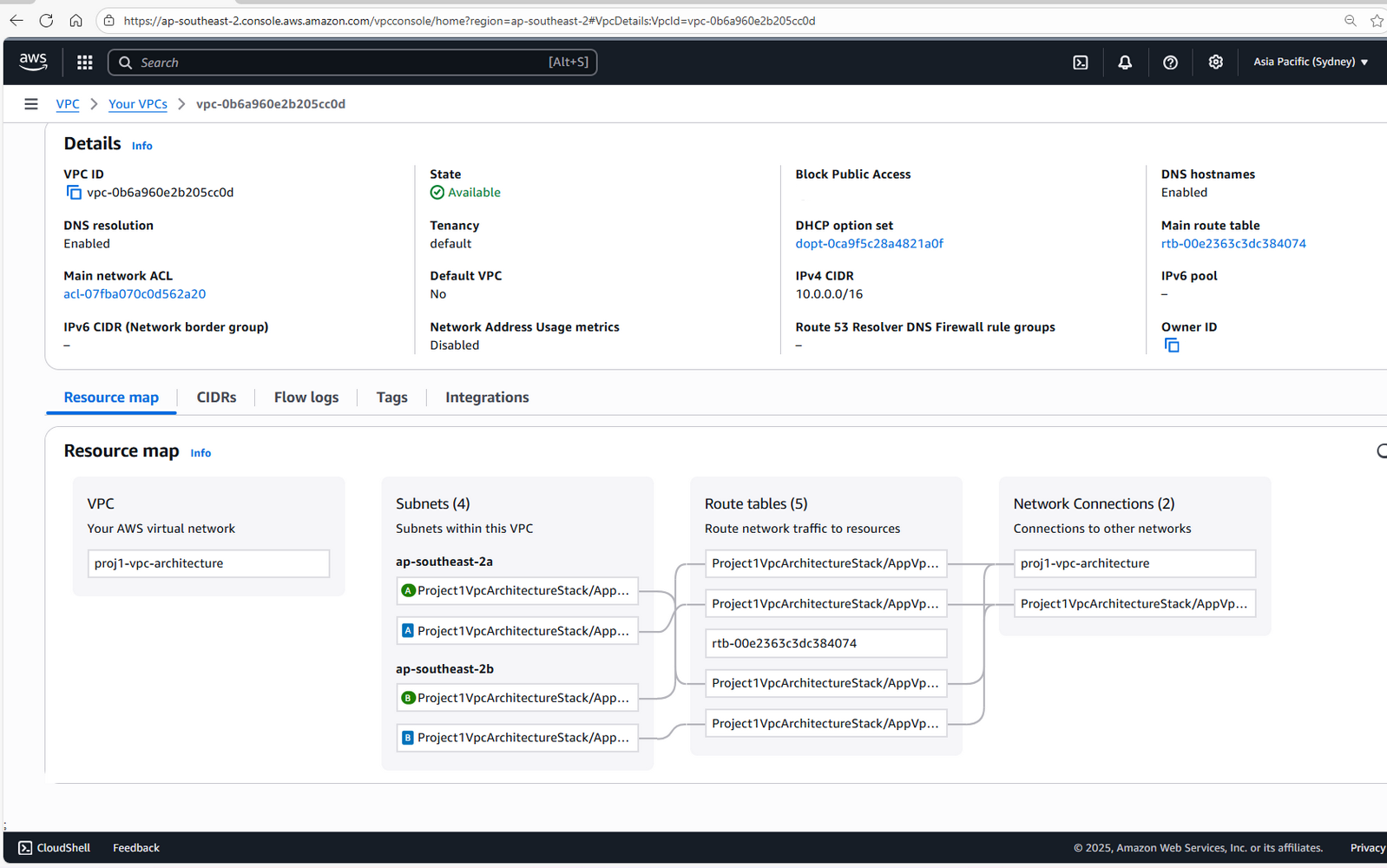
VPC Overview
Shows the created VPC and subnet mapping across Availability Zones.
Subnet List
Displays correct CIDR blocks and segmentation.
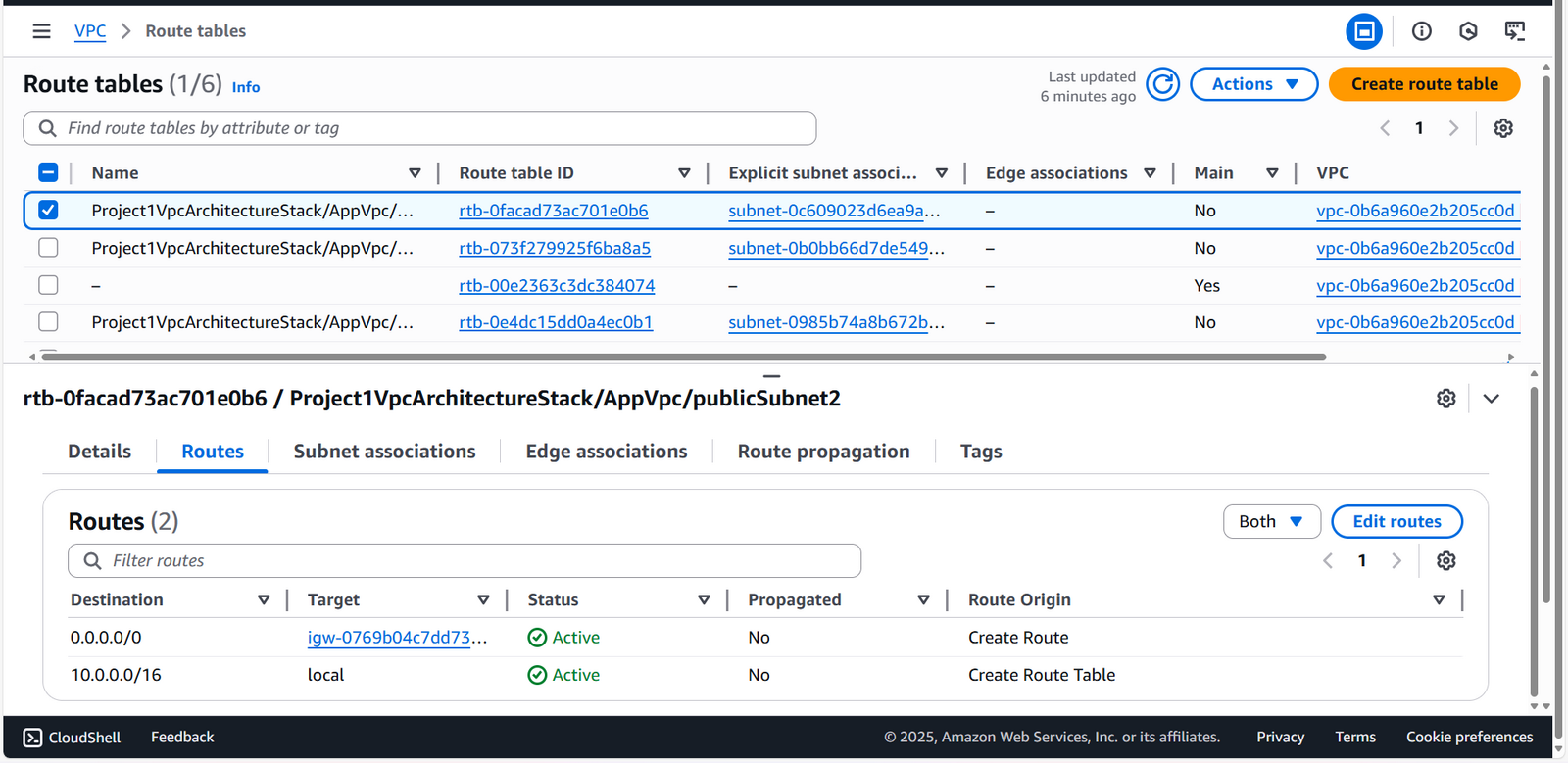
Route Tables
Confirm correct routing to IGW (public) and NAT Gateway (private).
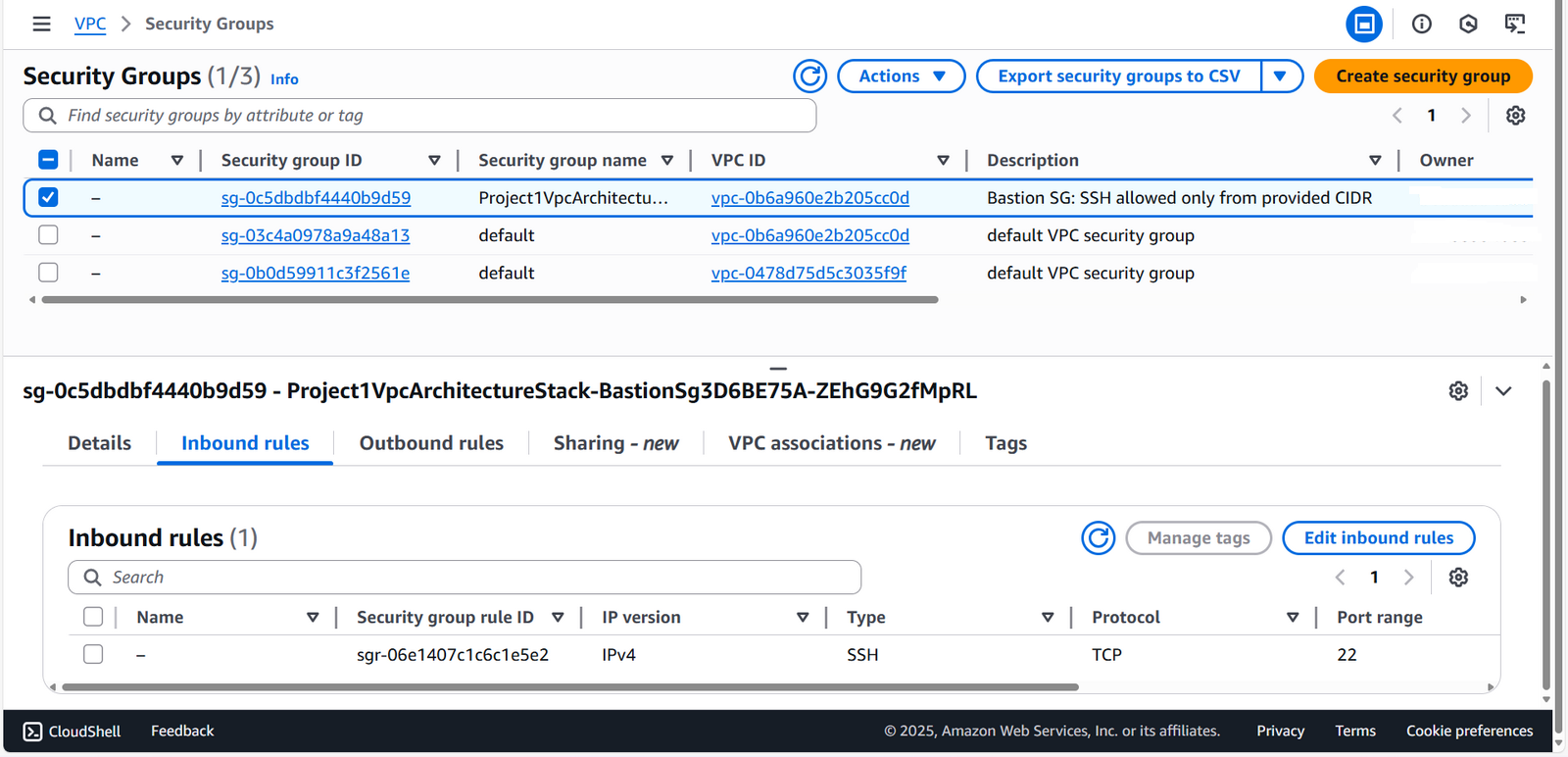
Security Groups
Shows restricted SSH ingress to the Bastion Host.
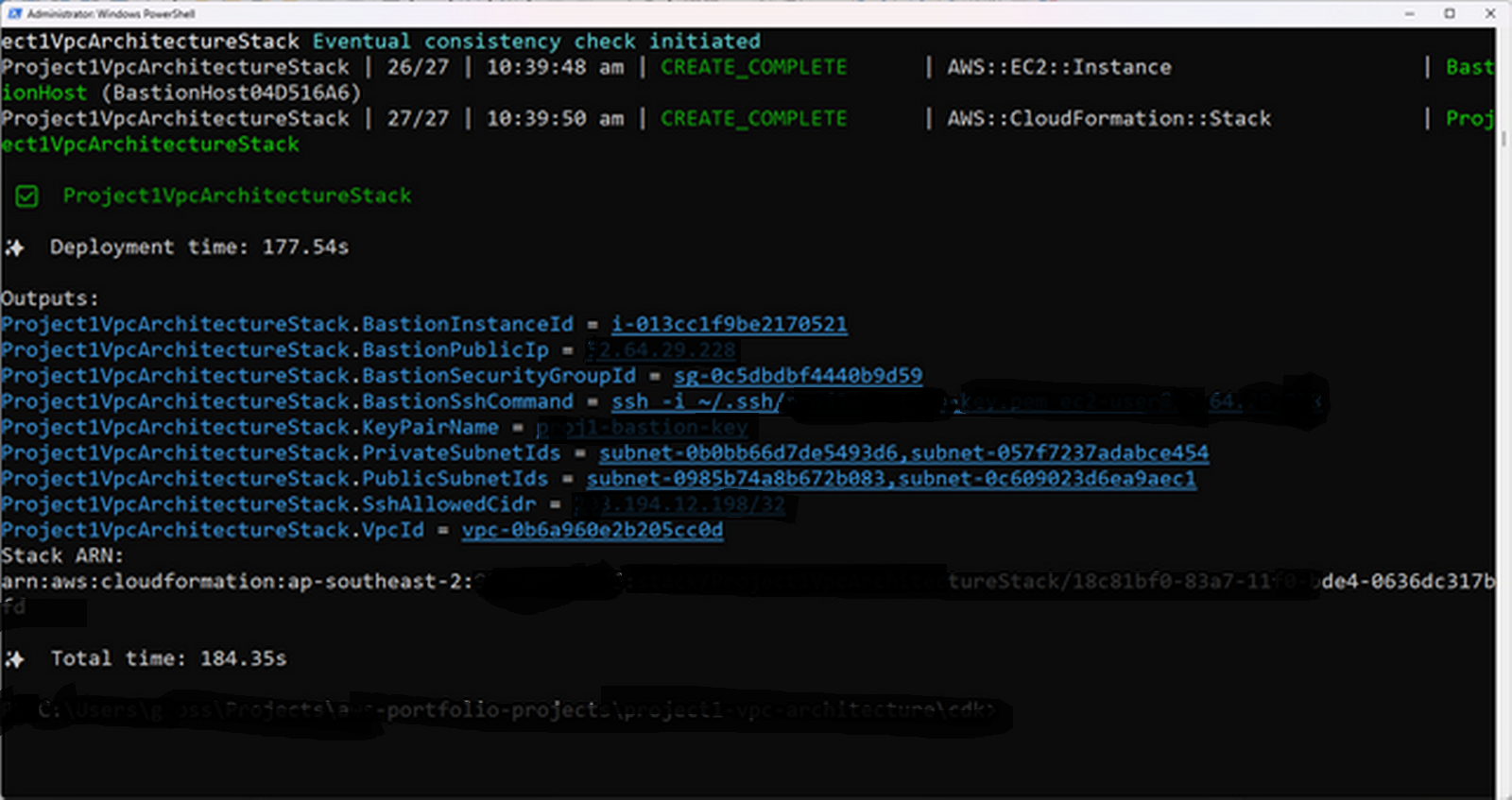
CDK Deploy Output
Successful provisioning of VPC, subnets, NAT Gateway, and Bastion Host.
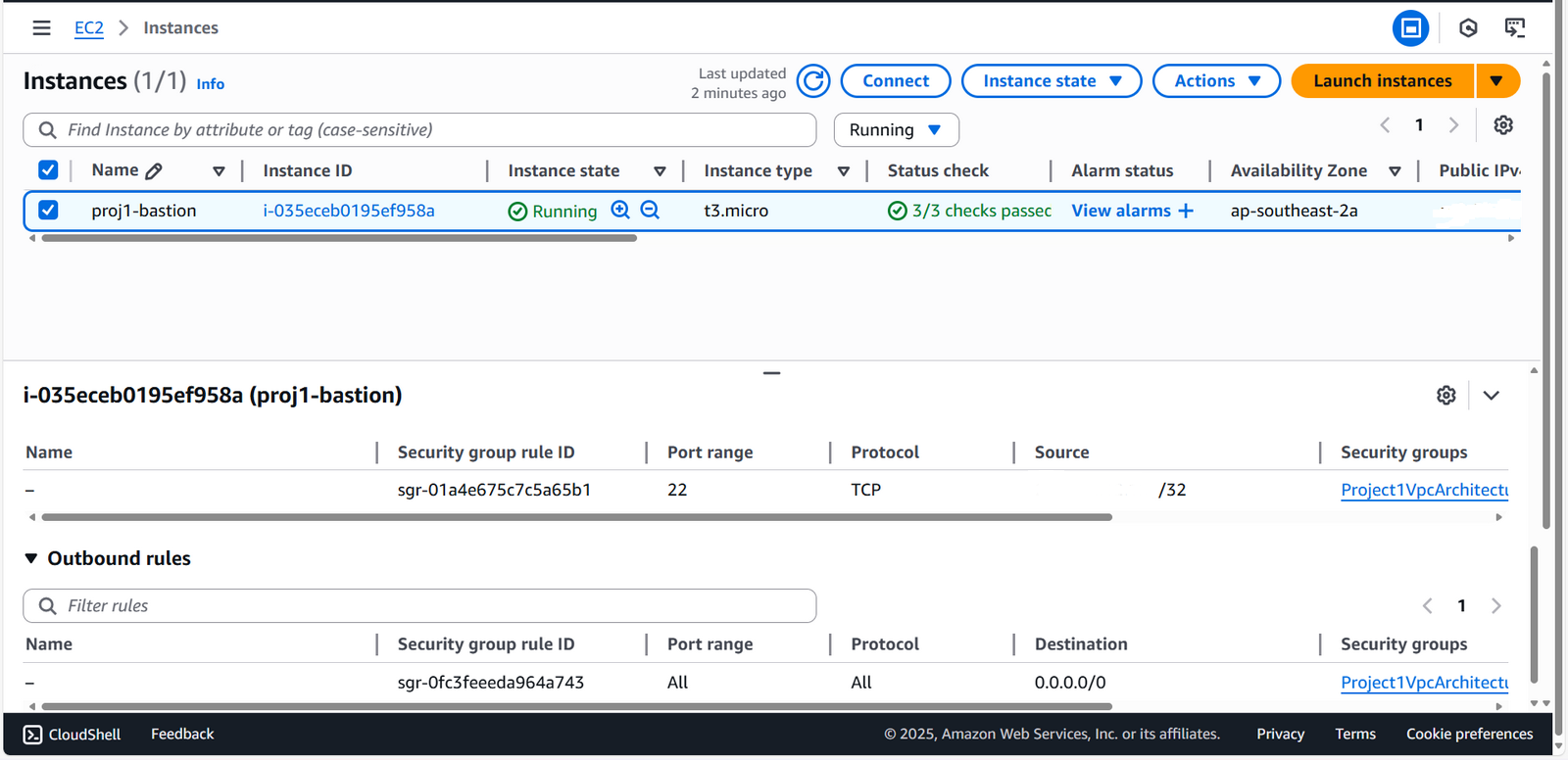
Bastion EC2 Instance
Deployed into the public subnet with the expected configuration.
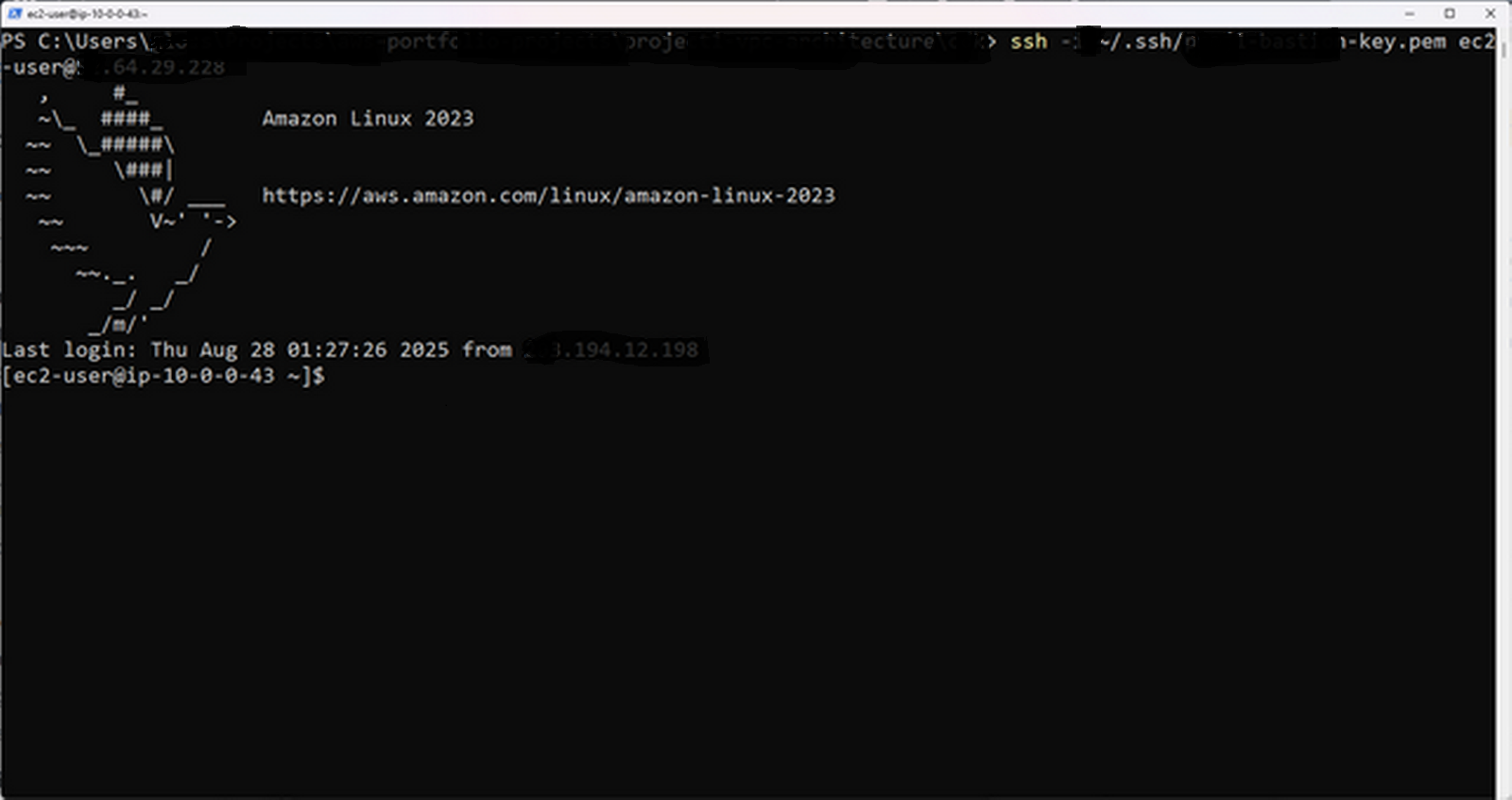
SSH Access to Bastion Host
Verifies routing, subnet segmentation, and security group rules.
🛠️ Improvements Added
- Added subnet segmentation across two Availability Zones
- Implemented NAT Gateway for secure outbound access
- Restricted Bastion Host SSH access using a controlled CIDR
- Replaced manual network setup with Infrastructure as Code
🧭 Possible Enhancements
These features align with natural next steps for production environments:
- Replace Bastion Host with SSM Session Manager
- Add VPC Flow Logs for traffic analysis
- Deploy multiple NAT Gateways for full high availability
- Introduce VPC Endpoints to reduce NAT Gateway dependency
- Add CloudWatch Alarms for route and instance monitoring
⚠️ Failure Scenarios & Mitigations
| Scenario | Mitigation |
|---|---|
| NAT Gateway failure | Deploy NAT Gateway in a second AZ |
| Bastion Host unreachable | Validate SG ingress + assign Elastic IP |
| Incorrect routes | CDK-defined routing reduces misconfigurations |
| Accidental exposure | Private subnets have no IGW route by design |
🎯 Expected Outcomes
- Demonstrate strong understanding of AWS networking fundamentals
- Show capability to design secure, segmented cloud networks
- Provide a reusable VPC foundation for later portfolio projects
- Highlight Infrastructure-as-Code skills with AWS CDK
🧩 Challenges & Solutions
- Route table debugging: Verified routing behaviour through console tests
- CIDR allocations: Used clear /24 segmentation for readability
- SSH restriction: Implemented deploy-time context variable for dynamic CIDR control
🪞 Reflection / Lessons Learned
- Building networks with IaC significantly reduces error-prone manual steps
- Segmented VPCs provide a strong baseline for secure architectures
- Using a Bastion Host is a great way to demonstrate controlled administrative access, while leaving room to evolve toward more modern approaches like SSM Session Manager
- Documenting decisions (ADR) improves clarity and interview discussions
📘 GitHub Repository:
https://github.com/nicolasgloss-dev/secure-vpc-architecture
📄 Architecture Decision Record:
https://github.com/nicolasgloss-dev/secure-vpc-architecture/blob/main/adr.md